SSH In Case Of
Note: Putty officially recommends to use Bitvise SSH Client & Server.
See also:
- Eternal Terminal (ET) with Tmux mode
- Powershell.
Sudo #
sudo without passwd
vim /etc/sudoers
# or
sudoedit /etc/sudoers
modify ALL=(ALL) ALL to ALL=(ALL) NOPASSWD:ALL (i.e. add NOPASSWD: before the last ALL), e.g.
%sudo ALL=(ALL:ALL) NOPASSWD:ALL
SSHD Config > Less Time #
Add two commands to avoid long time before asking passwords:
GSSAPIAuthentication no
UseDNS no
GSS API is alternative to SSH-keys
SSHD Config > More Security #
Change to get high security by using key auth only:
PasswordAuthentication no
ChallengeResponseAuthentication no
SSHD Config > Keep Alive #
On server:
ClientAliveInterval 100
ClientAliveCountMax 2
(this can also be done on clients, but usually clients_nr > server_nr.)
Config > Remember to Restart #
sudo service ssh restart
SSHDConfig > All Above Together #
echo ' ' >> /etc/ssh/sshd_config;
echo 'GSSAPIAuthentication no' >> /etc/ssh/sshd_config;
echo 'UseDNS no' >> /etc/ssh/sshd_config;
echo 'PasswordAuthentication no' >> /etc/ssh/sshd_config;
echo 'ChallengeResponseAuthentication no' >> /etc/ssh/sshd_config;
echo "ClientAliveInterval 100" | sudo tee -a /etc/ssh/sshd_config
echo "ClientAliveCountMax 2" | sudo tee -a /etc/ssh/sshd_config
echo ' ' >> /etc/ssh/sshd_config;
service ssh restart && sleep 1 && service ssh status
SSHD To Allow Root Login w/ Password #
Note: dangerous, use for tests only.
sed -i 's/.*PermitRootLogin.*//' /etc/ssh/sshd_config
echo 'PermitRootLogin yes' >> /etc/ssh/sshd_config
sed -i 's/.*PasswordAuthentication.*//' /etc/ssh/sshd_config
echo 'PasswordAuthentication yes' >> /etc/ssh/sshd_config
service ssh restart && sleep 1 && service ssh status
-i: using public key (e.g. ~/.ssh/id_rsa) as the identity for authentication.
Client Config File Example #
vi ~/.ssh/config
# with the following config, we can `ssh mydb`
Host mydb
HostName 10.40.2.2
Port 22
User opc
ProxyJump [email protected]
# Jump through multiple hosts:
# ProxyJump user@host1,user@host2,user@host3
# VNC 5901 port: // On Windows you can see it referenced as :0 which means 5900, :1 is 5901 etc.
LocalForward 5901 localhost:5901
# test web
LocalForward 80 localhost:8080
# or
LocalForward client_local_ip_like_127001:80 remote_server:8080
# Reversed forwarding
RemoteForward 90 localhost:9999
# or
RemoteForward sever_ip:90 client_localhost:9999
# SOCKS
DynamicForward 1337
SSH Tunneling for Clients #
port forwarding - direct static forwarding #
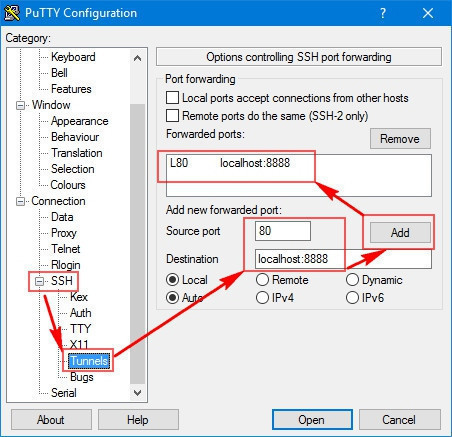
Suppose we want the client to Listen on80 and forward all traffic via SSH-server to localhost:8888 (a jupyter is running on “localhost” on the server).
ssh from nix as client: #
c2s (client-to-server) by -L #
ssh -L 80:localhost:8888 remote_server_username@remote_server_ip
-L: localforward, listen on a local client port and forward any connect (to this local client port 80) to the remote server.- meaning of this cmd: forward client’s local 80 (from ssh client’s perspective) to a specified server & port (localhost:8888, from ssh server’s perspective).
- the “localhost” in the cmd is the remote server.
s2c (server-to-client) by -R #
ssh -R 90:localhost:9999 remote_server_username@remote_server_ip
-R: remote reverse forward, listen on the remote server’s port and forward any connect (to server port 90) to this local client.- meaning of this cmd: forward remote (server) 80 to local end host & port (localhost:9999)
- the “localhost” in the cmd is this local client.
tips #
ssh -NR 90:localhost:9999 remote_server_username@remote_server_ip
ssh -fnNTqgR 90:localhost:9999 remote_server_username@remote_server_ip
this example shows common parameters used together with forwarding (note -R must be the last to combine with forwarding info).
-f: fork the process into the background after you type your password (may combine with sleep x, see man ssh).-n: no STDIN (n or N must be used if using -f).-N: no cmd execution on remote server, thus no remote terminal either (n or N must be used if using -f).-T: no pseudo-terminal allocation.-q: quiet mode. Since this is just a tunnel we can make it quiet.-g: globallly allow remote hosts to connect to local forwarded ports (must be specified on the master process for a multiplexed connection).
See ref zhihu for autossh.
ssh from win as client: #
port forwarding - dynamic port forwarding (socks proxy) #
client on nix: #
ssh -D 9876 -fnN -C -q -N myuser@remote_ssh_server
-D9876 : dynamic destinations, port 9876 behaves as a SOCKS server.-C: compression on.
client on win: #
putty ssh tunnels > source port 9876; dest: Dynamic.
bitvise > services > SOCKS proxy > enable > listen port 9876.
usage in firefox: #
about:config
network.proxy.no_proxies_on : localhost, 127.0.0.1, 192.168.0.0/24, .yourcompany.com
network.proxy.socks : 127.0.0.1
network.proxy.socks_port : 8080
network.proxy.socks.remote_dns : true
network.proxy.socks_version : 5
network.proxy.type : 1
permanent ssh tunneling as a service #
Create a persistent SSH tunnel between servers with systemd, (bak)
Generate Keys for Openssh-server #
(OBS: putty-gen can convert .ppk to openssh, but not vice-versa. cuz .ppk contains key pair.)
in windows with putty #
Run PUTTYGEN.EXE: (OBS: some servers requires > 2048)
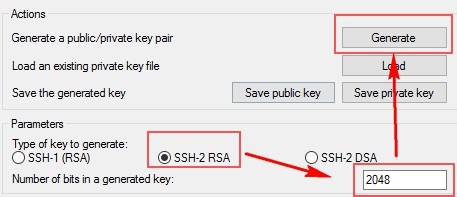
Result (3 files to download):
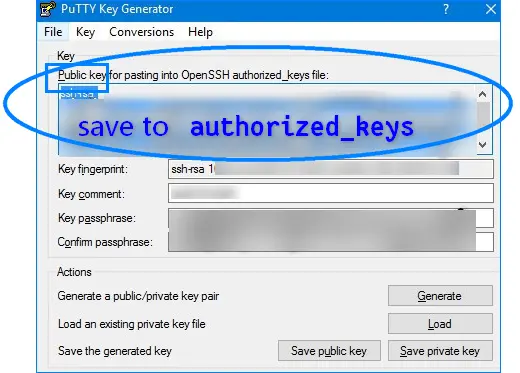

- Change “Key comment” !!! (will influence .ppk chucksum, so canNOT be easily changed later).
- Give passphrase (recommended).
- Copy the “public key for … authorized_keys” content to file
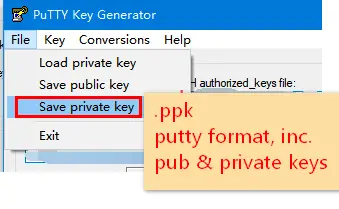
authorized_keys(OpenSSH, most Nix distribution). - “Save private key” to .ppk (putty format, inc. private & public pair).
- Menu > Conversions > “Export OpenSSH Key” > file
id_rsa(private, OpenSSH).
in nix #
Generate and distribute:
ssh-keygen -b 2048
# give fileanme or press enter for default
ssh-copy-id -i $HOME/.ssh/id_rsa.pub -p 22 username@host1
ssh-copy-id -i $HOME/.ssh/id_rsa.pub -p 22 username@host2
REMOVE FINGERPRINT CHECK INFO #
method 1: add fingerpring for all nodes #
(this may insert redundant/duplicate items if any is already exiting, but no problems.)
ssh-keyscan -H ip_domain_1,ip_domain_2,ip_domain_3 >> ~/.ssh/known_hosts
Batch from a file example:
ssh-keyscan -f $HADOOP_HOME/etc/hadoop/slaves -H >> ~/.ssh/known_hosts
method 2: permanently disable check (not recommended) #
ssh config:
Host *
StrictHostKeyChecking no
method 3: ssh w/ -o to each node to trigger auto-adding fingerprint
#
(why not use ssh-keyscan instead?)
ssh -oStrictHostKeyChecking=no 192.168.1.1
RUN A COMMAND ON REMOTE SERVER #
ssh user@host "echo \$HOME" # need to escape variables
RUN A SCRIPT ON REMOTE SERVER #
Nix as driver:
ssh [email protected] 'bash -s' < myscript.sh
Win as driver, see here.
DISABLE PROMPTS OF APT-GET (DIST-)UPGRADE / INSTALL GRUB #
sudo DEBIAN_FRONTEND=noninteractive apt-get -y -o Dpkg::Options::="--force-confdef" -o Dpkg::Options::="--force-confold" upgrade
Config Putty #
Mosh (Mobile-Shell) #
install on servers #
Nix:
sudo apt install mosh
install on clients #
Nix or Windows WSL:
sudo apt install mosh
Windows cygwin, if needs other termianl emulators (or simply use chrome):
C:\cygwin64\setup-x86_64.exe -q mobile-shell
C:\cygwin64\Cygwin.bat
run #
mosh host_or_ip
# or
mosh --ssh="ssh -p 80" user@host_or_ip
NOTE: here uses --ssh=... to set ssh port, as mosh -p means the mosh port, not ssh one.
udp ports range #
60000:61000
as mosh -p means the mosh port, not ssh one.